ENHANCE YOUR Cybersecurity & Compliance from aN Expense to a Strategic Advantage

Our mission
At ACTIVECYBER, it all begins with a commitment to protecting your most valuable asset: data. We are dedicated to providing cybersecurity solutions tailored to meet YOUR UNIQUE NEEDS. Whether it’s enhancing your cybersecurity posture, achieve compliance, or protect against emerging threats, our team is here to guide you every step of the way.

Industry-Leading Solutions
Advisory
-
Working with your C-Suite to develop custom strategies to enhance your cybersecurity posture.
Development of policies, procedures, and compliance leveraging industry-recognized best practices.
-
Selecting the appropriate framework(s) and develop a custom compliance roadmap for your organization.
Preparing for and conducting internal audits (e.g. ISO 27001, SOC 2, CMMC) prior to certification / attestation.
-
Identifying and mitigating cybersecurity risks based on risk methodology prescribed by NIST SP 800-30.
Detailed Risk Treatment Plan (RTP) for C-Suite decisions.
-
Helping to implement and adhere to cybersecurity policies and procedures.
Integrating new technologies and practices.
-
Company-wide training on cybersecurity best practices tailored to your organization.
Development of a security aware culture and curriculum.
-
Gain access to our experienced Chief Information Security Officers to guide your organization's cybersecurity efforts.
Work with internal stakeholders to prioritize risk-based decisions and security initiatives.
-
Determine inherit risk of critical vendors and suppliers.
Prioritize remediation efforts for each individual vendor based on residual risk to your critical data.
-
Review of your cloud instance (Azure, AWS, Google, etc.) against industry recognized best practices.
Provide ongoing cloud checks to maintain a secure instance.
Resiliency
-
Identifying security weaknesses.
Simulating attacks to test defenses.
-
Simulating sophisticated cyber-attacks.
Evaluating and improving detection and response.
-
Scanning for compromised information.
Alerting and preventing data misuse.
-
Training staff to recognize attacks.
Strengthening defenses against various social engineering attacks (e.g. phishing, vishing, SMSishing)
-
Reviewing application code for vulnerabilities.
Ensuring secure coding practices.
-
Analyzing web applications for vulnerabilities and exploitable threats.
Providing remediation recommendations and actions.
-
Analyzing cloud environments for vulnerabilities and exploitable threats.
Providing remediation recommendations and actions.
-
24 x 7 x 365 monitoring detects potential and ongoing threats across your networks, endpoints, and cloud environments
Rapid response to minimize damage and ensure security.
The ACTIVE Framework™: Your Comprehensive Guide to Cybersecurity Excellence
Explore our Six Pillar FRAMEWORK that Empowers Your Organization to Stay Ahead of Evolving Threats.
-
Strategy & Expertise: Leverage our in-depth knowledge and strategic insights to navigate the complexities of cybersecurity. We help you define a clear, effective security roadmap tailored to your organization’s unique needs.
-
Audit & Assessments: Ensure your organization meets or exceeds industry standards. We guide you through the necessary audits and assessments to maintain compliance and develop your strategic advantage.
-
Vulnerability, Penetration & Social Engineering Testing: Identify and address potential vulnerabilities before they can be exploited. Our comprehensive testing services simulate real-world attacks to strengthen your defenses.
-
Governance & Adoption: Deploy effective cybersecurity policies and procedures and ensure seamless adoption across your organization. We assist in embedding robust security metrics and measures into your daily operations.
-
Monitoring, Detection & Response: Gain 24 x 7 x 365 visibility into your networks, endpoints, and cloud environments to ensure swift and effective response to threats.
-
Evaluate & Train: Empower your team with the skills and knowledge needed to maintain a secure environment. Our training programs are designed to test your teams susceptibility to deliberate attacks and enhance awareness and preparedness against modern cyber threats.
Our ACTIVE FRAMEWORK™ supports:
ISO 27001
〰️
CMMC
〰️
NIST 800-171
〰️
NIST 800-53
〰️
GDPR
〰️
HIPAA
〰️
SOC 1
〰️
SOC 2
〰️
PCI DSS
〰️
ISO 27002
〰️
ISO 27701
〰️
ISO 14001
〰️
ISO 27017
〰️
ISO 27018
〰️
ISO 42001
〰️
ISO 22301
〰️
ISO 9001
〰️
ISO 27001 〰️ CMMC 〰️ NIST 800-171 〰️ NIST 800-53 〰️ GDPR 〰️ HIPAA 〰️ SOC 1 〰️ SOC 2 〰️ PCI DSS 〰️ ISO 27002 〰️ ISO 27701 〰️ ISO 14001 〰️ ISO 27017 〰️ ISO 27018 〰️ ISO 42001 〰️ ISO 22301 〰️ ISO 9001 〰️
“We believe cybersecurity is not prescriptive in nature; our ACTIVE Framework™ takes a tailored approach to understanding risks, demonstrating compliance and undertaking remediation efforts—each based on your risk appetite.”
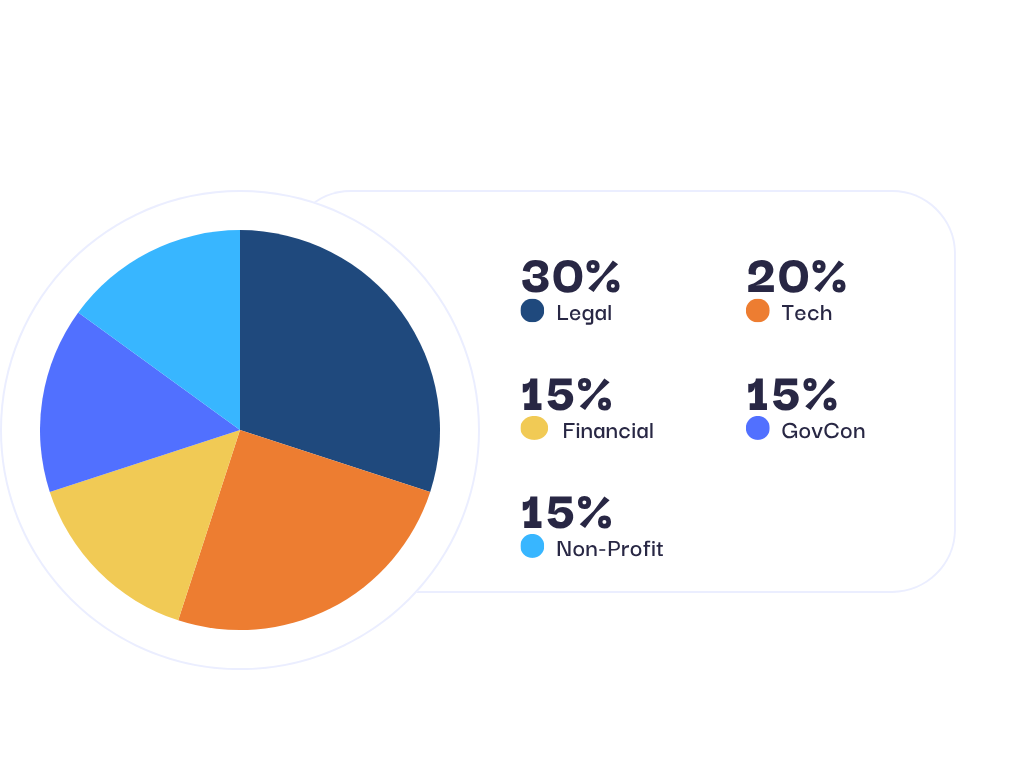
TAILORED Solutions for Every Industry
Whether you operate in Legal, Technology, Non-Profit, Financial, or GovCon sectors, our expert team at ACTIVECYBER understands your unique cybersecurity challenges.
We specialize in delivering bespoke solutions that protect your critical assets and ensure compliance with industry standards. Trust us to secure your digital future.
Our Client Portfolio
"ACTIVECYBER is known as THE cybersecurity leader in highly nuanced sectors like Legal, Non-Profit, and more."
Our performance speaks for itself
24
Years as Trusted Advisors
67%
New Client Growth via Referrals
6M+
Tests Performed on Vital Assets
20
CVE’s Published in NVD
100%
Certification Success
Rate
96%
Client Retention
Rate
Customers trust ACTIVECYBER to ensure their cybersecurity resilience
“With ACTIVECYBER’s assistance, we’ve enhanced our cybersecurity framework, and further positioned Steptoe as an innovative leader in legal services. ACTIVECYBER’s strategic expertise has strengthened our compliance and contributed to the evolution of industry security standards, solidifying prominence in legal cybersecurity.”
Don Sternfeld
Steptoe Chief Innovation Officer
prove you’re secure. DEMONSTRATE COMPLIANCE. maintain trust.