ACTIVELabs: Pioneering Cybersecurity Research and Innovation
ACTIVELabs identifies and discloses undiscovered vulnerabilities, leading the charge in securing our clients, partners, and the tech community.
Powered by ACTIVECYBER
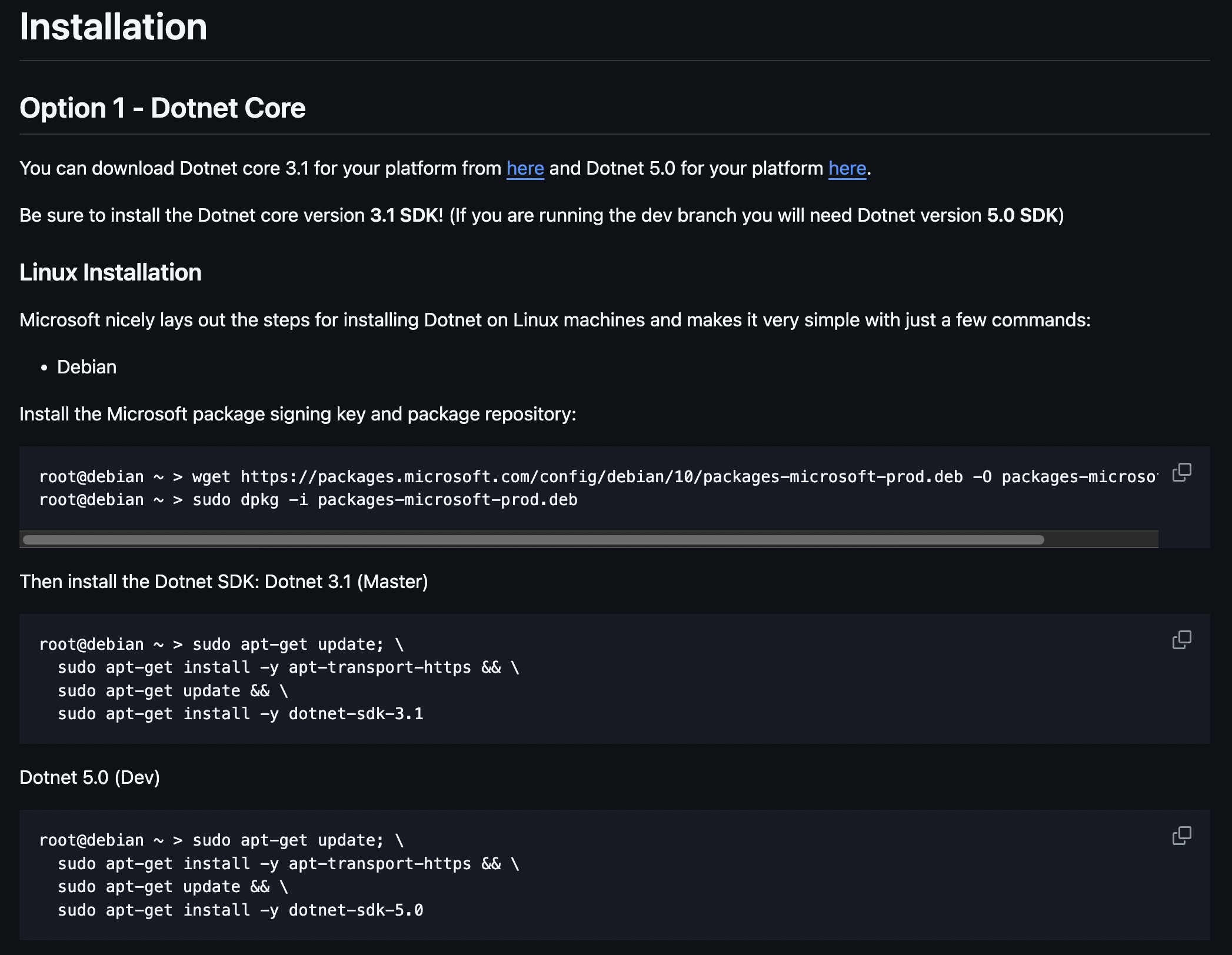
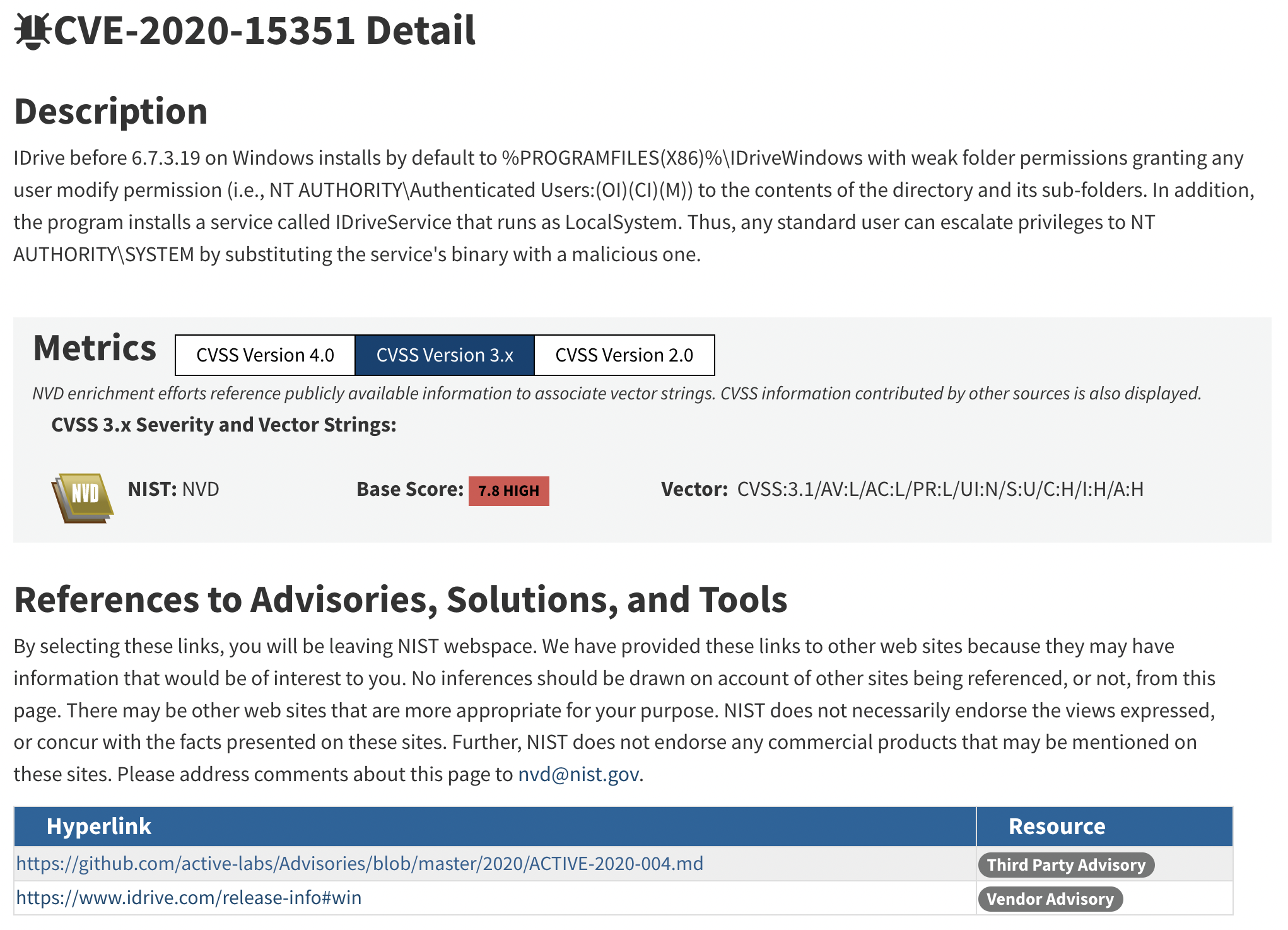
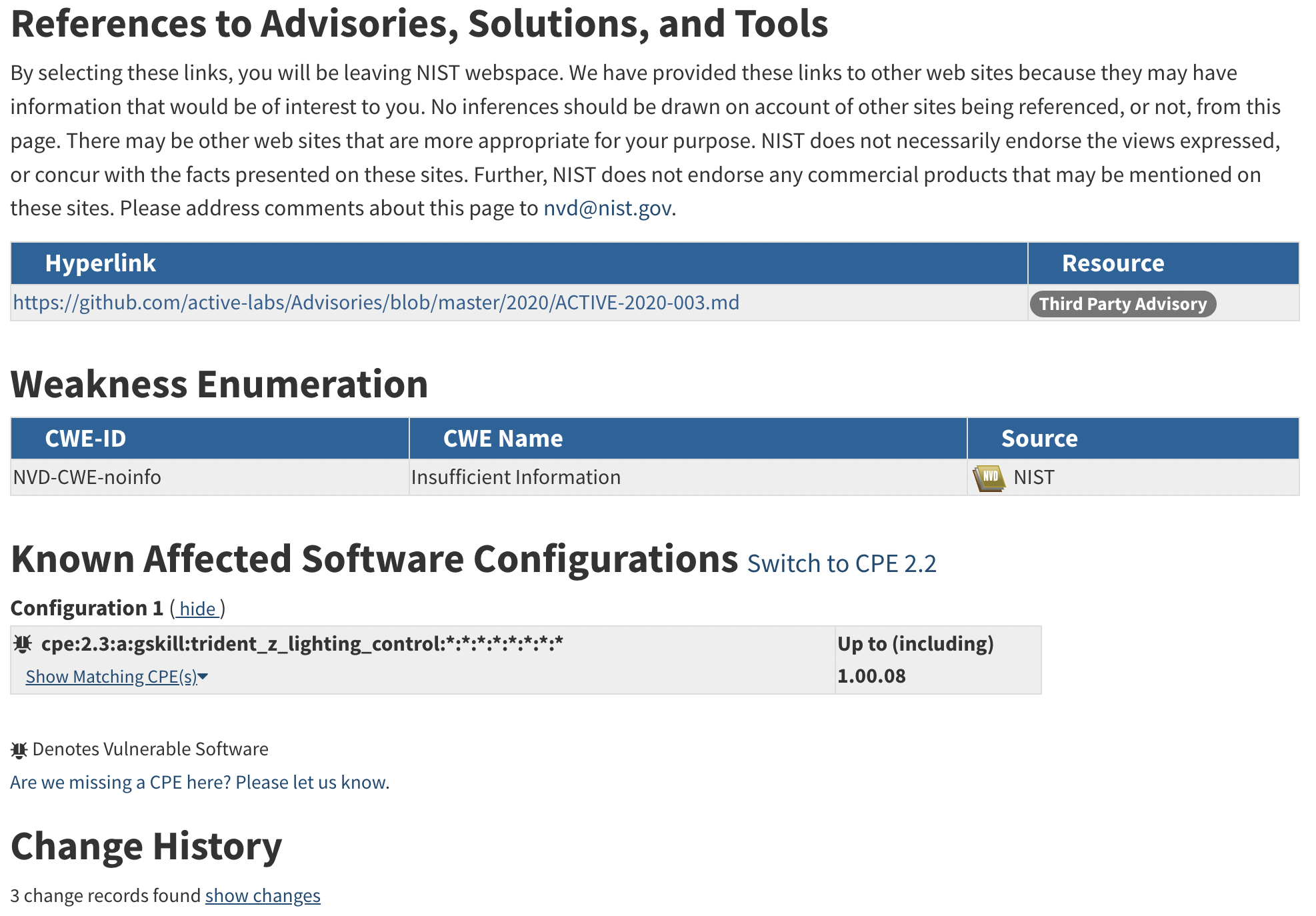
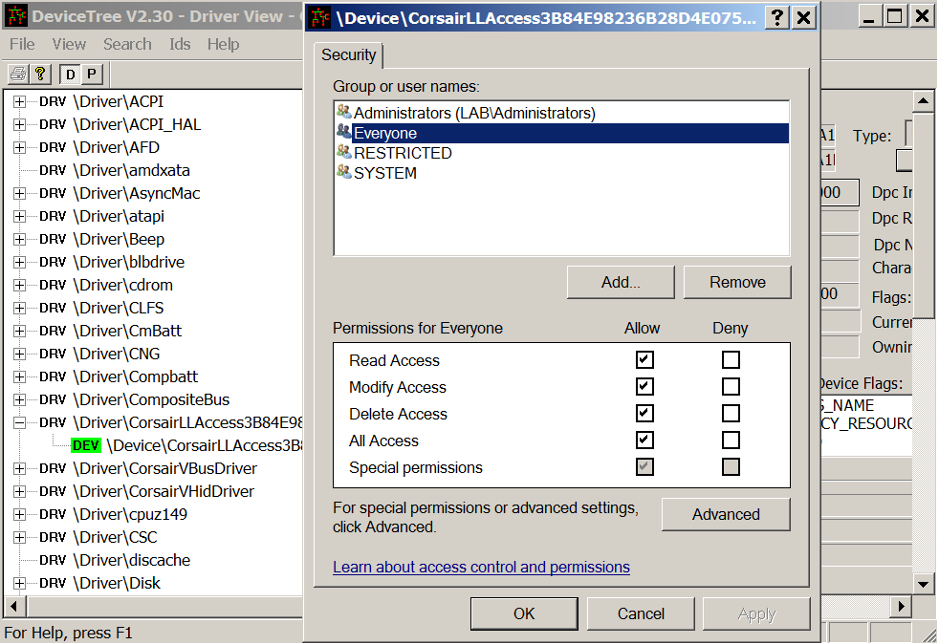
ACTIVELabs was created in 2018 to hunt and research undiscovered vulnerabilities, report them to vendors via responsible disclosure programs, publish advisories, develop and validate new patches, and to share this information for the advancement of the cybersecurity community. ACTIVELabs was established with the mission of securing our ever-growing client base, partnerships, and the technology community as a whole. We are actively providing the community with verified findings and research that leads to the creation of new Common Vulnerabilities and Exposures (CVEs) and updates to the National Vulnerability Database (NVD).


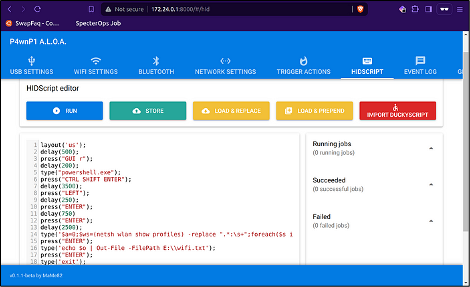
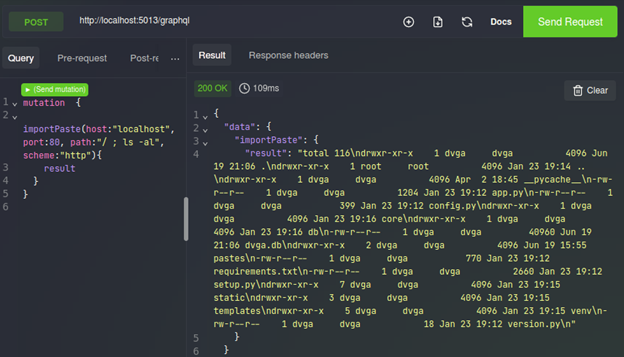
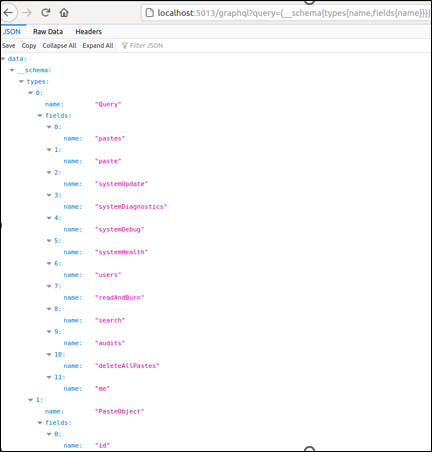
Hacking GraphQL: Attacking APIs
There are several application programming interfaces (APIs), each serving a different purpose and catering to a specific need. This post specifically focuses on the GraphQL API.